Introduction: The Illusion of Outsourced Safety
In the complex and high-stakes environment of modern healthcare, ensuring the safety and integrity of the facility, its patients, and its staff is a paramount concern. A critical component of this security apparatus is the robust management of third-party vendors, from medical device representatives and service technicians to consultants and contractors. To meet this need, a multi-billion-dollar industry of vendor credentialing companies has emerged, offering sophisticated platforms that promise to streamline compliance, mitigate risk, and create a secure operational environment. Industry leaders market their services as the very “backbone of healthcare operations” 1, a means to “empower healthcare organizations to… safeguard against threats, protect patient and employee safety” 2, and a commitment to “create safer healthcare environments for everyone”.3 Hospitals and health systems, in turn, invest significant resources in these services, operating under the assumption that they are outsourcing a critical risk management function to specialized experts.
This reliance, however, masks a profound and perilous disconnect between marketing promises and contractual reality. Consider a scenario that keeps risk managers awake at night: a credentialed vendor, vetted and approved through a third-party platform, commits a crime within the hospital—a theft of expensive equipment, a breach of sensitive patient data, or, in the worst case, an assault. Subsequent investigation reveals the vendor had a criminal record or a history of sanctions that the background check, processed by the credentialing company, failed to detect. The hospital, believing it had outsourced this very risk, turns to its credentialing partner. Who bears the legal and financial consequences of this catastrophic failure?
An exhaustive analysis of the terms and conditions governing these services reveals a stark and unsettling answer: the hospital does. This report uncovers the “Credentialing Paradox”—the phenomenon whereby healthcare organizations pay a premium for a risk-mitigation service, only to find that the provider’s legal agreements are meticulously engineered to disclaim all responsibility for accuracy and abdicate nearly all liability for failure. Through a deep dive into the legal fine print of major industry players, this analysis will demonstrate how risk is not transferred, but merely delegated, leaving the hospital fully exposed. This report will deconstruct the key contractual clauses that facilitate this risk transfer, provide a comparative analysis of the industry’s standard legal posture, and conclude with a set of actionable recommendations for healthcare leaders to navigate this landscape of outsourced processes and retained risk.
Section 1: Deconstructing the Fine Print – A Legal Deep Dive into Service Agreements
The foundation of the credentialing paradox lies buried in the dense legal language of Master Service Agreements (MSAs) and Terms of Use (TOU) that hospitals agree to, often with little negotiation. These documents, while appearing to be standard legal boilerplate, contain specific, powerful clauses that systematically dismantle the provider’s accountability and transfer the burden of risk squarely onto the client institution. A careful deconstruction of these clauses reveals a deliberate and consistent legal strategy across the industry.
The “As Is” / “As Available” Clause: The Foundation of Risk Transfer
The first and most fundamental tool used to shift risk is the “AS IS” and “AS AVAILABLE” clause. In a service contract, this language is not mere filler; it is a powerful legal disclaimer that serves to eliminate any implied warranties of quality, performance, or fitness for a particular purpose. When a hospital agrees to receive a service “AS IS,” it is contractually accepting the platform, software, and data in its current condition, with all its potential faults and errors, known or unknown. This single phrase effectively negates the reasonable expectation that a service purchased for a critical function like safety and compliance will be reliable or effective.
This is not an isolated practice but a universal standard across the vendor credentialing industry. An examination of the legal agreements of major players reveals a consistent pattern:
- symplr, through its terms, states unequivocally: “The Service is provided on an ‘AS IS’ and ‘AS AVAILABLE’ basis, with all faults”.4
- GHX echoes this sentiment in its credentialing terms for providers: “GHX PROVIDES ALL SERVICES HEREUNDER ‘AS IS'”.5
- Green Security uses nearly identical language, informing users that it “provides the Site and Site Content ‘AS IS’ for use at the user’s own risk”.6
- Verisys reinforces this position across its legal documents, stating, “THE SERVICE IS PROVIDED ‘AS IS,’ WITHOUT WARRANTY OF ANY KIND WHATSOEVER” 7 and, in its broader legal notice, “VERISYS PROVIDES THEIR WEBSITES ‘AS IS,’ ‘WITH ALL FAULTS’ AND ‘AS AVAILABLE'”.8
- IntelliCentrics follows the same model, specifying in its SEC3URE platform terms that “The Platform and Services are provided ‘AS IS’ without warranty of any kind”.9
The strategic implication of this universal clause cannot be overstated. A hospital engages a credentialing service with the implicit goal of ensuring vendors are properly screened and safe to be on-site. This goal presupposes a service that is functional, reliable, and fit for that specific purpose. The “AS IS” clause directly and legally contradicts this core business purpose. It is the contractual equivalent of the service provider stating, “We provide you with access to this credentialing platform, but we make no promises about its quality, its functionality, or whether it will actually help you achieve your safety objectives.” From the very outset of the legal relationship, the risk of service failure is placed on the hospital. The institution is not purchasing a guaranteed outcome of safety or accuracy; it is merely licensing access to a tool, and it bears the full risk of that tool’s potential inadequacies. This forms the legal bedrock upon which all subsequent, more specific disclaimers are built.
The Myth of Guaranteed Accuracy: Explicit Disclaimers of Warranty
Moving beyond the general “AS IS” provision, these companies employ even more specific and alarming disclaimers that target the very essence of their service: the accuracy of the data they provide. While their marketing materials promote concepts like “human-reviewed, AI-assisted credential verification” 10 and “real-time verification” 11, their contracts tell a different story. The terms and conditions explicitly state that they do not warrant the correctness, completeness, reliability, or timeliness of the credentialing information they process and deliver.
The evidence of this practice is widespread and unambiguous:
- symplr makes “no warranty” that “the results that may be obtained from use of the Service will be accurate or reliable”.4
- GHX is even more direct, stating it “HEREBY DISCLAIMS ALL IMPLIED. WARRANTIES, INCLUDING, WITHOUT LIMITATION, WARRANTIES OF… ACCURACY OF DATA”.5
- Green Security provides a comprehensive disclaimer, asserting it “DOES NOT WARRANT THE ACCURACY, RELIABILITY, TIMELINESS, QUALITY, SUITABILITY, TRUTHFULNESS, AVAILABILITY OR COMPLETENESS OF THE SITE CONTENT” and goes so far as to warn that “Errors and misprints may occur”.6
- Verisys, while marketing its ability to “Transform incomplete, flawed provider data” 8, states in its legal notice that “Information on this website is not promised or guaranteed to be correct, current, or complete, and this site may contain technical inaccuracies or typographical errors”.8 It further “expressly disclaims responsibility” for updating the information to keep it current.
- IntelliCentrics makes clear that its governing entities “make no warranties about the accuracy, reliability, completeness, timeliness, or results of use of the Platform”.9
- This practice is even international, as seen on the Verisys UK site, which states, “Neither we nor any third parties provide any warranty or guarantee as to the accuracy, timeliness, performance, completeness or suitability of the information… You acknowledge that such information and materials may contain inaccuracies or errors”.12
These clauses create what can only be described as a “liability vacuum.” The hospital, seeking to offload the operational burden and associated risk of vendor screening, outsources the process of verification. However, through these contractual disclaimers, it fully retains the risk of inaccurate verification. The credentialing company is positioned to profit from facilitating the process without being legally or financially accountable for the quality of its output. This dynamic creates a significant moral hazard. The business model incentivizes the credentialing company to prioritize scale, processing speed, and user acquisition over methodical, guaranteed accuracy, as there is no contractual penalty for being wrong. If the data provided is flawed—a criminal conviction is missed, a sanction is overlooked, a license is expired—and that flaw leads to harm within the hospital, the institution has no legal recourse to claim that the credentialing company breached a warranty of accuracy. The hospital is left to face the legal, financial, and reputational fallout alone, while the credentialing company has already collected its fees for the very service that failed.
The Burden of Truth: Shifting Responsibility for Data Accuracy to the User
The final piece of this risk-shifting architecture is perhaps the most audacious. Not only do these companies disclaim responsibility for the accuracy of their own data, but they also contractually place the burden of providing true and correct information squarely on their users—both the vendors submitting their credentials and the hospital client consuming the service. This fundamentally reframes their role from that of an independent verifier to that of a passive data conduit.
The contractual language makes this shift in responsibility explicit:
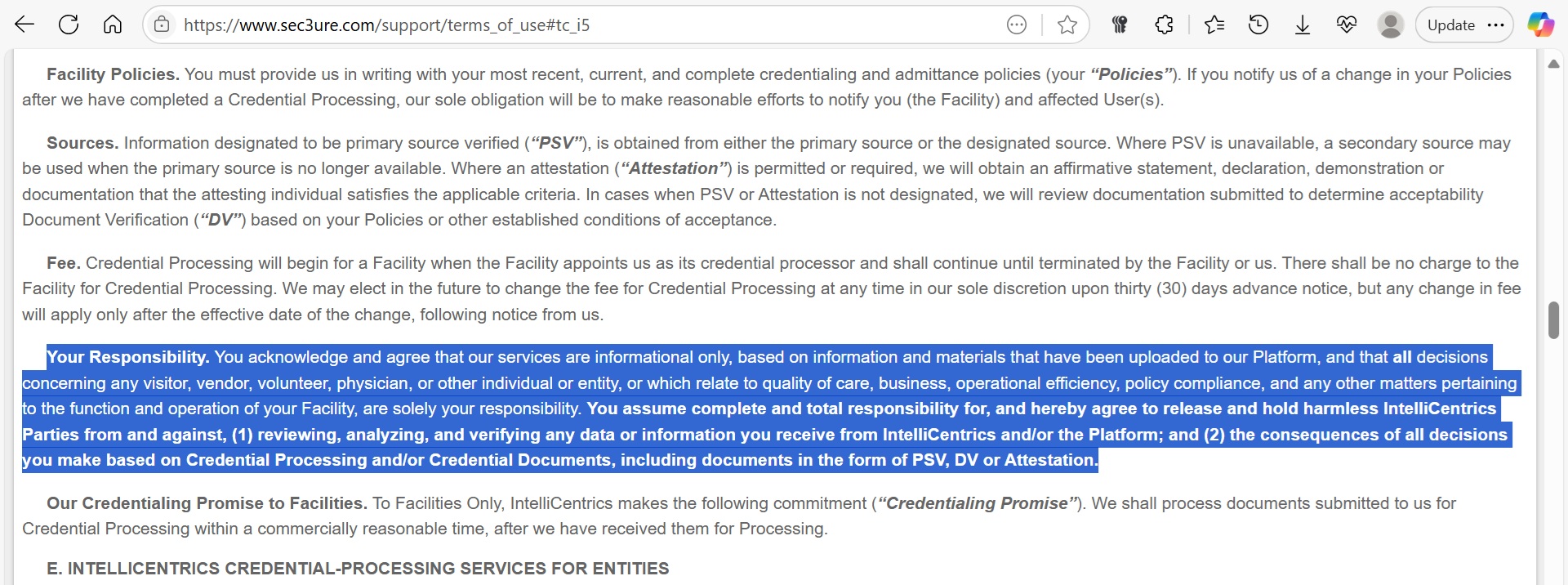
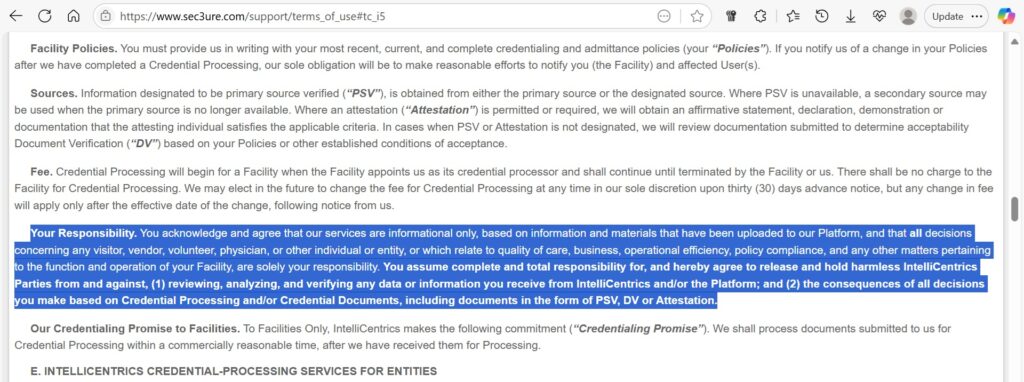
- IntelliCentrics is exceptionally clear on this point. Its terms state, “You are solely responsible for… keeping all data submitted by you or for you… accurate, current, and not misleading”.9 It further clarifies that its services are “informational only, based on information and materials that have been uploaded to our Platform,” and that the hospital client must “assume complete and total responsibility for… reviewing, analyzing, and verifying any data or information you receive”.9
- symplr’s “Credentialing Service Master Terms” codify this responsibility, stating that the “Customer shall provide complete, accurate, and current provider Information”.13 The agreement then absolves symplr of accountability for any negative outcomes, noting it “will not be liable… for any loss, cost, or expense” that arises from the customer’s failure to provide accurate information.13
- Green Security requires its users to agree that “all credentialing information provided will be accurate, complete, current, truthful and in made in good faith”.6
- Verisys places a similar burden on its users, who must “warrant that all of the information that you have provided is correct and complete to the best of your knowledge and belief”.7
This contractual framework reveals that the business model is not truly “verification-as-a-service” but rather “data-aggregation-as-a-service.” The platforms function as sophisticated databases and workflow tools that collect, store, and display information provided by others. Their legal agreements are constructed to reflect this reality, even if their marketing language suggests a more active, authoritative, and independent verification role. This creates a circular logic that undermines the entire premise of third-party verification. The platform’s “verified” status is predicated on the user’s own unverified assertion of accuracy. The hospital, therefore, is paying a third party to manage a process that ultimately relies on the truthfulness of the very vendors it seeks to vet. The platform is a database manager, not a guarantor of truth.
Section 2: Capping the Consequences – The Power of Limitation of Liability
Even if a hospital were able to overcome the formidable hurdles of “AS IS” clauses and warranty disclaimers and successfully argue in court that a credentialing company was negligent, the legal battle would still be largely symbolic. A second layer of contractual defense ensures that any potential financial recovery for the hospital is capped at a commercially insignificant amount, rendering the service provider effectively immune to the real-world consequences of its failures. This is achieved through two powerful and universally applied clauses: Limitation of Liability and the Exclusion of Consequential Damages.
A “Limitation of Liability” clause sets a hard ceiling on the total amount of money a service provider can be required to pay in damages, regardless of the actual harm caused. An “Exclusion of Consequential Damages” clause goes a step further, specifically barring claims for indirect losses that result from the initial failure. This is a critical distinction, as in a healthcare setting, the most significant damages—patient lawsuits, regulatory fines under statutes like HIPAA, loss of public trust, and business interruption—are all considered “consequential” or “indirect” damages. By excluding these, the credentialing company insulates itself from the most catastrophic financial risks its clients face.
The contractual caps set by these companies are often shockingly low, bearing no relation to the magnitude of risk involved in healthcare operations:
- IntelliCentrics provides the most stark example. Its terms state that its maximum liability “will in no event and under no theory exceed the lesser of a) the amount paid by the respective party to IntelliCentrics during the year preceding the event giving rise to the claim, or b) US $100”.9 For a multi-million-dollar health system, a liability cap of one hundred dollars is not a risk allocation strategy; it is a near-total abdication of financial responsibility.
- symplr employs a similar tactic, capping its liability at the greater of US$50 or the amount paid by the customer for the service in the preceding 12 months.4 A separate document for its credentialing services limits liability to the amount paid for the specific service that gave rise to the claim.13
- GHX sets its cap at the “aggregate the total fees paid by you to GHX for the services during the 12 months immediately preceding the date of the first event giving rise to any claim against GHX”.14 While seemingly more reasonable than a $100 cap, this still means that if a catastrophic failure occurs, the hospital’s maximum recovery is limited to one year’s worth of service fees, a figure that would be dwarfed by the actual damages.
Crucially, all major providers with available terms—including symplr, GHX, IntelliCentrics, and Green Security—explicitly disclaim liability for “indirect, incidental, special, exemplary, punitive or consequential damages”.4
The combination of these aggressive liability caps and the broad exclusion of consequential damages renders the credentialing company a “judgment-proof” partner in the event of a major safety incident. This legal architecture has profound financial implications. Imagine a scenario where a credentialing failure leads to an incident causing $5 million in damages to a hospital, comprising legal fees, a patient settlement, and regulatory fines. The hospital sues the credentialing company for negligence. Even if the court finds the company at fault, the terms of the service agreement would cap the company’s financial liability at, for example, the $25,000 in annual fees the hospital paid. In the case of IntelliCentrics, the recovery could be as low as $100. The hospital and its insurers are left to cover the remaining $4,975,000 loss. The risk has not been mitigated or shared; it has been fully and contractually retained by the hospital, which paid for a service that ultimately offered no financial protection. This forces the hospital’s own insurance carriers to bear the full cost of a claim that was precipitated by the failure of a third-party service, which can, in turn, lead to increased insurance premiums for the hospital in the future.
Section 3: Comparative Analysis – How the Industry Leaders Manage Liability
To fully appreciate the systemic nature of this risk-transfer model, it is essential to compare the legal postures of the industry’s leading vendor credentialing companies side-by-side. The following analysis demonstrates that the use of broad disclaimers and severe liability limitations is not the practice of a few outliers but rather a standardized, industry-wide strategy. This pattern is critical for healthcare leaders to understand, as it indicates that the underlying problem of retained risk cannot be solved simply by switching from one major vendor to another. Instead, it necessitates a more fundamental, strategic approach to managing the inherent risks of using any such third-party platform.
The table below serves as the central exhibit of this report, synthesizing the key contractual clauses from symplr, GHX, IntelliCentrics, Green Security, and Verisys. It provides an at-a-glance view of how each company contractually addresses warranties, liability, and the responsibility for data accuracy.
| Company | Key “Disclaimer of Warranty” Language | Key “Limitation of Liability” Language | Stated Liability Cap | Burden of Accuracy Placed on User? |
| symplr | “The Service is provided on an ‘AS IS’ and ‘AS AVAILABLE’ basis… [no warranty that] results will be accurate or reliable.” 4 | “…shall not be liable for any indirect, incidental, special, exemplary, punitive or consequential damages…” 4 | Greater of US$50 or amount paid in preceding 12 months. 4 | Yes. Customer must provide “complete, accurate, and current” information. 13 |
| GHX | “PROVIDES ALL SERVICES HEREUNDER ‘AS IS.’…DISCLAIMS ALL IMPLIED. WARRANTIES, INCLUDING… ACCURACY OF DATA” 5 | “…neither GHX nor its affiliates… will be liable for any direct, indirect, punitive… consequential, or other damages…” 14 | Aggregate fees paid during the 12 months preceding the claim. 14 | Yes. User represents submitted material is “accurate”. 14 |
| IntelliCentrics | “Platform and Services are provided ‘AS IS’… make no warranties about the accuracy, reliability, completeness…” 9 | “…maximum liability… will in no event… exceed the lesser of a) the amount paid… during the year… or b) US $100.” 9 | Lesser of US$100 or fees paid in the preceding year. 9 | Yes. User is “solely responsible” for keeping data “accurate, current, and not misleading.” 9 |
| Green Security | “‘AS IS’ for use at the user’s own risk… DOES NOT WARRANT THE ACCURACY, RELIABILITY, TIMELINESS…” 6 | “In no event shall the Company… be liable for any indirect, incidental, special, exemplary, or consequential damages…” 6 | Not explicitly quantified in snippets, but consequential damages are disclaimed. | Yes. User agrees “all credentialing information provided will be accurate, complete, current, truthful.” 6 |
| Verisys | “‘AS IS,’ WITHOUT WARRANTY OF ANY KIND…”.7 “Information… is not promised or guaranteed to be correct, current, or complete…” 8 | “…not liable for the defamatory, offensive or illegal conduct of other users or third parties…” 7 | Not explicitly quantified in snippets, but certain damages are disclaimed. | Yes. User warrants that “all of the information that you have provided is correct and complete.” 7 |
The pattern revealed in this comparison is undeniable and deeply concerning for any healthcare organization that relies on these services. The legal frameworks of all major vendor credentialing companies are fundamentally aligned in their approach to risk. They operate as technology platforms that facilitate the aggregation and display of data while using their service agreements to build a fortress of legal insulation. This framework ensures that they are protected from the financial and legal consequences of data inaccuracy, service failure, or the criminal or negligent acts of the vendors they credential. The risk, despite the marketing claims of enhanced safety and compliance, remains firmly with the client hospital.
Section 4: The Hospital’s Dilemma – Navigating a Landscape of Delegated Risk
The contractual architecture meticulously constructed by vendor credentialing companies creates a significant dilemma for their hospital clients. The legal analysis translates into tangible operational, legal, and financial risks that must be actively managed by the hospital’s leadership. Ignoring the chasm between the marketed promise and the contractual reality can lead to a false sense of security and severe consequences.
The Operational Gap
Within a hospital, a dangerous operational gap can form. The compliance, safety, and supply chain departments often operate with the expectation that the credentialing service is a reliable, vetted solution that provides a definitive check on vendor safety. They see the “green check” on a vendor’s badge as a seal of approval. Simultaneously, the hospital’s legal and procurement departments, if they have closely reviewed the contract, understand that the service comes with no guarantees and near-zero liability for the provider. This disconnect can permeate the organization, leading to an over-reliance on a system that is contractually designed to be fallible. Front-line staff may grant access based on the credentialing badge alone, believing a thorough and guaranteed verification has occurred, when in fact the hospital has contractually agreed that no such guarantee exists.
The Legal Exposure
This operational gap creates significant legal exposure for the hospital. In the event of an incident involving a vendor, a plaintiff’s attorney could make a powerful argument based on legal doctrines such as “negligent credentialing” or “vicarious liability.” The hospital’s defense that it relied on a leading third-party credentialing service would be severely undermined by the service’s own terms and conditions. An opposing counsel could argue that the hospital’s reliance on a service that explicitly disclaims the accuracy of its own results 4 and limits its liability to a pittance 9 was, in itself, an act of negligence. The hospital cannot credibly shift blame to the vendor credentialing company when its own contract demonstrates that it knowingly accepted the service “AS IS” and agreed that the provider was not responsible for the accuracy of the verification. The contract, intended to protect the credentialing company, becomes a powerful piece of evidence against the hospital, demonstrating that the hospital was contractually aware of the service’s limitations and accepted the associated risks.
The Financial Implications
The financial consequences of this dilemma are stark. The hospital effectively pays twice for risk management. First, it pays the annual subscription or registration fees to the credentialing company for a service that provides little to no financial backstop. Second, in the event of a failure, the hospital and its insurers are left to pay for the full, uncapped damages resulting from the incident. This includes legal defense costs, settlements or judgments, regulatory fines, and the costs associated with reputational damage and patient remediation. This double payment highlights the fundamental misalignment of incentives. The credentialing company’s revenue is secure regardless of its performance, while the hospital’s financial stability is directly tied to the real-world outcomes of the credentialing process. Over time, a pattern of claims stemming from such incidents could also lead to a significant increase in the hospital’s liability and E&O insurance premiums, as insurers re-evaluate the hospital’s risk profile in light of the fact that it is retaining nearly 100% of the risk associated with its vendor population.
Conclusion & Actionable Recommendations for Healthcare Leaders
The vendor credentialing industry presents a profound paradox to healthcare leaders. These platforms are marketed as essential risk-mitigation solutions, promising to create safer, more compliant healthcare environments. However, a deep analysis of their standard service agreements reveals a starkly different reality. They are contractually structured as risk-transfer vehicles, employing a consistent and effective legal strategy—built on “AS IS” clauses, explicit disclaimers of accuracy, and severe limitations of liability—to shift the full weight of responsibility for verification failures onto the client hospital. The result is that hospitals pay for the illusion of outsourced safety while contractually retaining the entirety of the risk.
To navigate this challenging landscape, healthcare executives must move beyond marketing promises and engage directly with the contractual realities of these services. The following actionable recommendations provide a strategic playbook for mitigating the risks inherent in the current vendor credentialing model.
1. Conduct an Immediate Legal and Risk Review of Your Credentialing Service Agreement
The first and most urgent step is to treat the vendor credentialing service agreement as a high-stakes contract, not as a simple software license. The marketing materials that promise a “backbone of healthcare operations” 1 or the ability to “safeguard against threats” 2 are not the legally binding terms. The actual terms of service govern the relationship.4 The hospital’s risk management, legal, and procurement teams must collaborate on a thorough review of the current agreement to identify the specific disclaimer language, liability caps, and exclusions of damages. Understanding the precise nature and scope of the risk the hospital has retained is a non-negotiable prerequisite for managing it effectively.
2. Implement a “Trust, but Verify” Protocol
Given the universal and explicit disclaimers of accuracy found in these agreements 4, vendor credentialing platforms must be treated as a first-pass administrative filter, not as a definitive source of truth. Hospitals cannot afford to operate under the assumption that a “green check” is an ironclad guarantee. A “trust, but verify” protocol should be developed as a necessary supplement. This involves creating a risk-based internal verification process for vendors who have the highest levels of access, such as those who enter sterile environments, interact directly with vulnerable patient populations, or handle sensitive data. This may involve conducting a secondary, independent background check or verifying critical credentials directly with the primary source. While this approach partially defeats the purpose of outsourcing, it is a crucial step to mitigate the significant risk the hospital has contractually retained.
3. Re-evaluate and Document Your Due Diligence Process
The legal analysis makes it clear that true due diligence cannot be fully outsourced under these standard industry agreements. The hospital’s internal due diligence policies and procedures must be updated to reflect the known limitations of its third-party platform. This process should be meticulously documented. This documentation is critical for defending against potential future claims of negligent credentialing. It should demonstrate that the hospital understood the platform’s limitations and implemented reasonable, supplementary measures to address the residual risk. This proactive documentation can transform the hospital’s position from one of naive reliance to one of informed and prudent risk management.
4. Engage in Proactive Contract Negotiation
While these terms are often presented as non-negotiable, large hospitals and health systems possess significant leverage, particularly during initial procurement or contract renewal. This leverage should be used to negotiate more favorable and balanced terms. Key targets for negotiation should include:
- Raising Liability Caps: Challenge the commercially absurd liability caps (e.g., $100 or $50) and negotiate for a cap that is more aligned with the potential for real-world damages.
- Requesting Service-Level Agreements (SLAs): Push for specific SLAs with financial penalties for the vendor’s failure to meet defined accuracy or timeliness benchmarks. This can create a contractual carve-out to the broad “AS IS” disclaimers and introduce a level of financial accountability for performance.
- Requiring Adequate Insurance: Mandate that the credentialing vendor carries a substantial Errors & Omissions (E&O) insurance policy and insist that the hospital be named as an additional insured on that policy. This provides a potential path for recovery through the vendor’s insurer.
5. Educate Internal Stakeholders
Finally, it is imperative to close the operational gap between perception and reality within the hospital. All internal stakeholders, from department heads and unit managers to front-line security and administrative staff, must be educated on the true nature of the vendor credentialing system. Training should emphasize that the “green check” on a vendor’s badge signifies only that an administrative process has been completed; it is not an absolute guarantee of safety or compliance provided by an infallible authority. Fostering a culture of awareness, vigilance, and appropriate skepticism is essential. This human element must complement, rather than be replaced by, the technology platform, creating a more resilient and genuinely secure healthcare environment.
Works cited
- symplr, the leader in healthcare operations, accessed August 1, 2025, https://www.symplr.com/
- About – Green Security, accessed August 1, 2025, https://gogreensecurity.com/about
- Vendormate Credentialing & Compliance – GHX, accessed August 1, 2025, https://www.ghx.com/media/1urkosxl/vendormate_suppliers_brochure_2024.pdf
- symplr Value Analysis, accessed August 1, 2025, https://secure.greenlightmedical.com/terms-of-use
- Master Service Agreement – GHX, accessed August 1, 2025, https://www.ghx.com/media/bxtcyoqe/ghx-credentialing-on-line-terms-and-conditions-provider-rev-05-2020.pdf
- Green Security, accessed August 1, 2025, https://www.greensecurityllc.com/terms-of-service
- Policies and Terms of Service – Verisys, accessed August 1, 2025, https://verisys.com/policies-and-terms-of-service/
- Legal Notice – Verisys, accessed August 1, 2025, https://verisys.com/legal-notice/
- IntelliCentrics’ SEC 3 URE Terms of Use, accessed August 1, 2025, https://www.sec3ure.com/support/terms_of_use
- Providers – Green Security, accessed August 1, 2025, https://gogreensecurity.com/providers
- Top 10 Medical Credentialing Companies In U.S – Capline Dental Services, accessed August 1, 2025, https://www.caplinedentalservices.com/top-10-medical-credentialing-companies-in-u-s/
- Terms of Use – Verisys, accessed August 1, 2025, https://www.verisys.org.uk/terms-of-use
- Credentialing Service Master Terms | symplr, accessed August 1, 2025, https://www.symplr.com/wp-content/uploads/2024/08/Credentialing-Services-Master-Terms.pdf
- Vendormate Service Package Terms rev 4-6-23 – GHX, accessed August 1, 2025, https://www.ghx.com/media/kz5fjlsm/vendormate-service-package-terms-rev-4-6-23-28.pdf